When implementing Agentforce there are two types of masking. Let me show you exactly how each works with real examples:
1. Pattern-Based Masking
Think of this as your intelligent guardian. It uses advanced pattern matching and machine learning to spot sensitive data. Here's what I've seen in practice:
Real Examples of Pattern-Based Masking:
Original Text:
Customer John Smith called about his account 123-45-6789. His email is john.smith@company.com and phone is (555) 123-4567.Please update his credit card ending in 4532.
Masked Result:
Customer [PERSON_NAME] called about his account [SSN]. His email is [EMAIL] and phone is [PHONE_NUMBER]. Please update his credit card ending in [LAST_4_DIGITS].
The system automatically detected and masked:
- Names (even without specific formatting)
- Social Security Numbers (based on the XXX-XX-XXXX pattern)
- Email addresses
- Phone numbers
- Credit card information
2. Field-Based Masking
This is your systematic protector, using Salesforce's existing metadata structure. Here's how it works in practice:
Example Using Prompt Builder with Field-Based Masking:
Original Merge Field Template:
- Account: {!Account.Name}
- Contact: {!Contact.FirstName} {!Contact.LastName}
- SSN: {!Contact.Social_Security_Number__c}
- Balance: {!Account.Account_Balance__c}
Masked Result (based on field classification):
- Account: [COMPANY_NAME]
- Contact: [FIRST_NAME] [LAST_NAME]
- SSN: [SSN]
- Balance: [CURRENCY_AMOUNT]
What happened here:
- Account.Name was masked because it's marked as Business Confidential
- Contact fields were masked due to PII classification
- SSN field was masked due to Platform Shield Encryption
- Balance was masked due to financial data classification
How it works
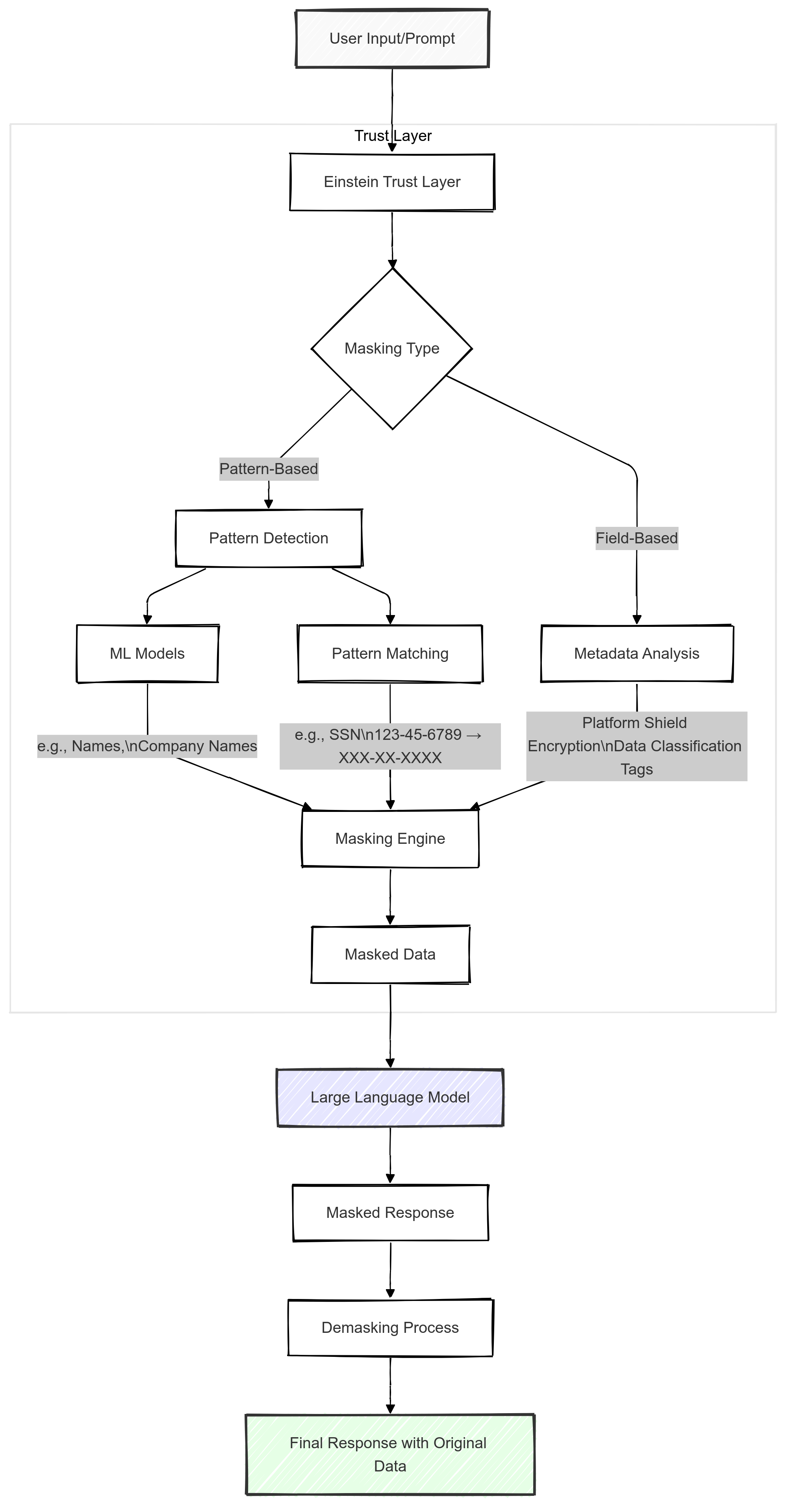
Below you can find a diagram of how data masking works, the process goes as follows:
- Input: User submits data/prompt
- Trust Layer immediately processes it through:
- Pattern-Based: ML + pattern matching for unstructured data (SSNs, names)
- Field-Based: Uses Salesforce metadata tags for sensitive fields
- LLM Processing: Receives masked data, processes request
- Output: System de-masks response, user sees original data
How to Set Up Both Masking Types
Let me walk you through the typical setup
- Pattern-Based Setup:
- Navigate to Setup → Einstein Trust Layer
- Enable Pattern-Based Masking
- Select the types of data to mask (Names, Email, Phone, etc.)
- Field-Based Setup:
- Set up Field-Level Security first
- Apply Platform Shield Encryption where needed
- Add Data Classification tags to sensitive fields
- Enable Field-Based Masking in Einstein Trust Layer
Real-World Testing Scenario
Here's a quick test I always run with clients to verify both masking types:
Test Input:
"Hi, I'm helping Sarah Jones with account 12345. Her SSN is 234-56-7890 and her premium is $50,000. Please email her at sarah.j@company.com."
Expected Masked Output:
"Hi, I'm helping [PERSON_NAME] with account [ACCOUNT_NUMBER]. Her [SSN] and her premium is [CURRENCY_AMOUNT]. Please email her at [EMAIL]."
Conclusion
The key for setting up data masking is understanding your data, implementing both masking types appropriately, and maintaining regular monitoring.
